identity authentication
Why Omnichannel Fraud Is a Growing Concern Today’s customers interact with auto dealerships and...
In the middle of a busy Tuesday afternoon, the shipping manager at a regional logistics hub...
Note: This story is based on the real experiences and stories shared with us by our customers. All...
Economic downturns have long been a catalyst for fraud. During tough times, the vulnerabilities of...
Let’s face it—the car rental game is under siege. Fraudsters are stepping up their tactics, and no...
The countdown is on! IGA 2025 is set for March 31 – April 3, 2025, at the San Diego Convention...
Data leaks are no longer isolated incidents; they’ve regretfully become a recurring headline in the...
No one wants to face a significant loss, especially in the equipment rental industry where the...
You might be asking yourself; do I really need to pay for another service? Sometimes it seems like...
The reality is identity fraud has and will continue to rise. Over recent years, we have seen...
In today's digital age, hiring a contractor for home improvement projects has become easier than...
Recent trends in fraud have created the imperative to authenticate the identity of your customers...
Fraudsters are becoming increasingly sophisticated in their methods, making it ever more essential...
Car theft has been a persistent issue for decades, causing significant financial losses and...
In the fast-paced world of real estate, it's essential to stay one step ahead of fraudsters.Real...
PALIDINDMV, a Driver’s License (DL) data verification check spanning 40 states, is now available as...
IDscan.net recently released a report, Fake ID Report 2023, which reveals crucial insights into the...
What is a Notary Public?
Fraudsters continue to use various nefarious methods to defraud liquor businesses and consumers...
Keep your liquor store on the right side of law enforcement.
Underage drinking. We all know it’s a problem, but how prevalent is it really? According to the USA
A customer walks up to your front desk. They flash an ID and hand over a credit card displaying the...
To stay competitive in the Auto Rental Industry it is essential that the renting process is fast,...
A new March 29, 2022 report by Javelin Research revealed that identity fraudsters continue to steal...
“Buy online, pickup in store” (BOPIS) has become ubiquitous. According to an article by Digital...
One of the most vital questions that confront managers of public-facing operations today concerns...
Just how prevalent is Credit Card Fraud today? The Federal Trade Commission’s Annual Data Book of...
Here’s a real-life scenario that one of our customers described to us - The shipping yards operated...
When you think about the selfie, your first thought likely is not about how useful it can be in the...
What to do when they win! ID authentication should be a fundamental step anytime a “qualifying...
Incidences of Identity-Theft Related Cargo Theft are on the rise
As our world continues to shift further into the realm of the internet, so do our buying habits. A...
Online gaming had been growing steadily over the past 10-15 years, but the COVID-19 pandemic threw...
The customer standing in front of you seems like a safe bet; they have an ID document with a photo...
In the restaurant biz, CCPs or "Critical Control Points" are key individual steps in the food...
Incumbent banking institutions have emerged out of the pandemic to a landscape scattered with...
As of this writing in June 2021, fraud and cyber crimes are running rampant and unabated throughout...
Trust what we cannot see? The best security might be completely invisible and hands-off to us, with...
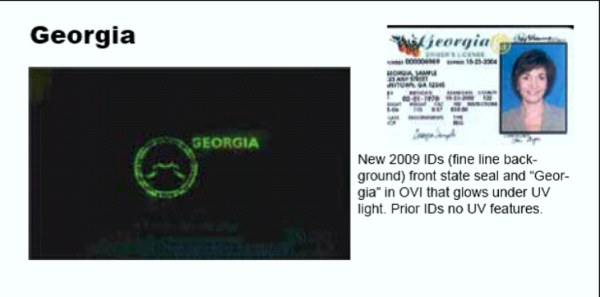
Countries around the world are designing ever-more intricate (and beautiful!) UV security features...
At this point, the concept of identity theft has thoroughly pervaded our popular lexicon and...
As of this writing in early March 2021, COVID19 vaccine deployments have given society a proverbial...
Ah, the Selfie. Equal parts necessary vacation documenter to cringe worthy "maybe that wasn't such...
Cashiers and Tellers Report Unable to “Feel” whether Money is Real or Not During our twenty years...
Information up-to-date as of April 24, 2019.
When it comes to assessing your risk of identity theft and fraud, being digitally compromised in a...
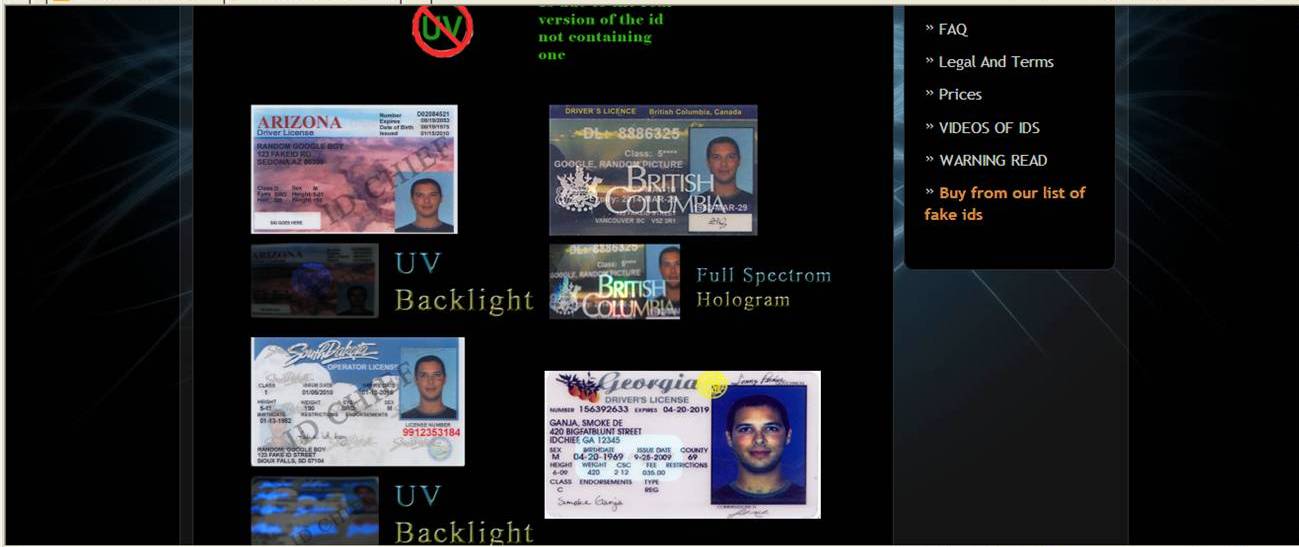
Several weeks ago, we began getting calls from a few clients asking us whether specific versions of...
You know it’s important to protect your business against fraud, but how do you protect your...
The California DMV released its Real ID-compliant driver license and identification (ID) card on...
If you are in noncompliance with Form I-9 requirements, your business could pay a rather hefty...
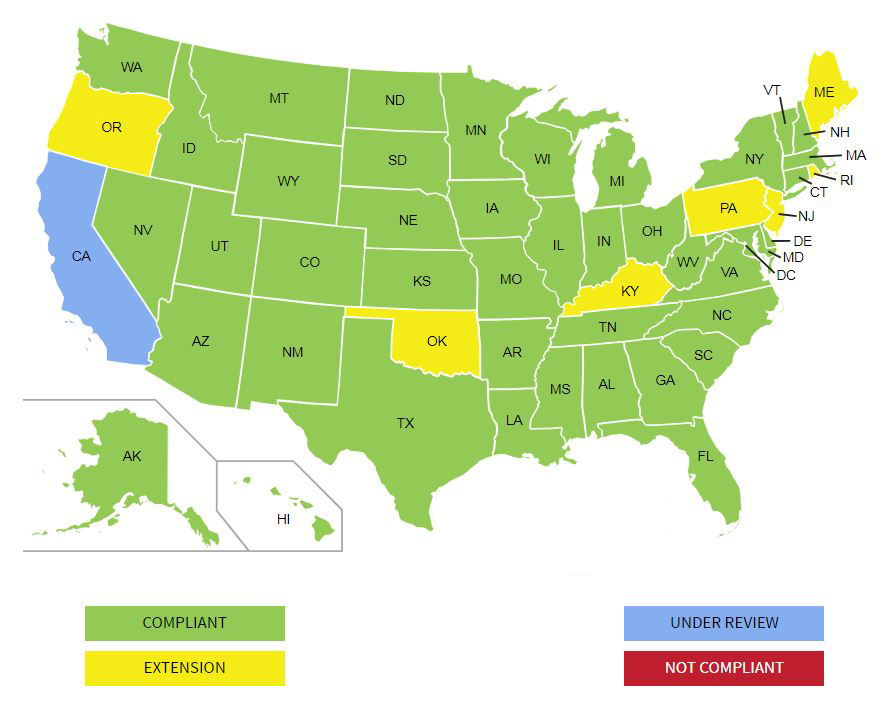
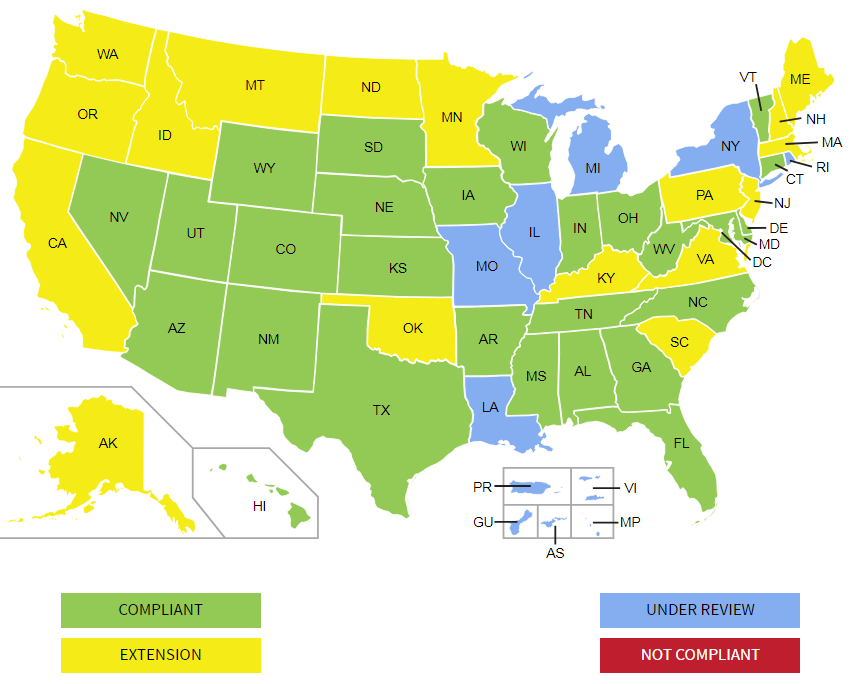
Many states are changing driver's license and identification card designs in next two years - which...
I found the below article so compelling, and so important as it relates to the current environment...
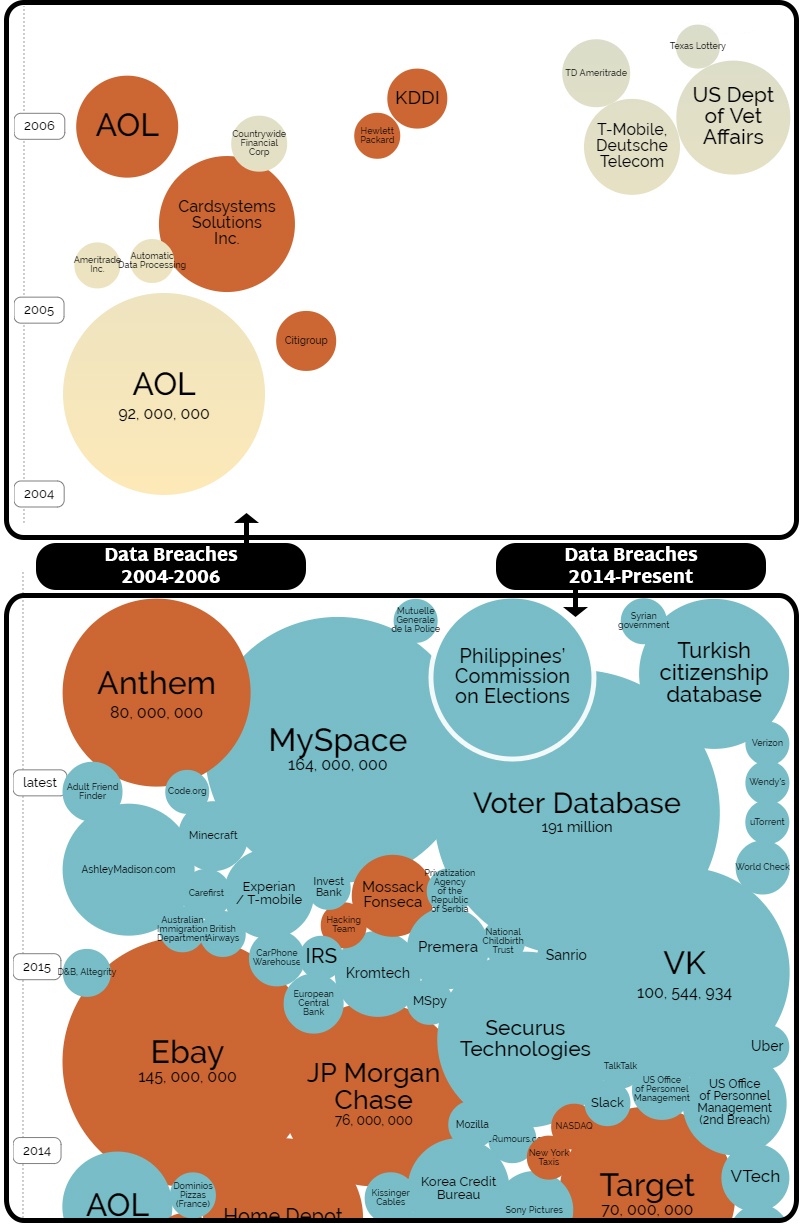
How the release of personally identifying information (PII) of nearly half the US population should...
• TABLE OF CONTENTS •Equifax Hack: The FactsHow Criminals Can Use This Stolen DataIdentity...
Retailers are on course to lose more than $70 billion globally to remote “card-not present” (CNP)...
• TABLE OF CONTENTS •Remote BankingMobile Client Onboarding is the Next FrontierMobile Identity...
Identity Theft continues to rank as the fastest growing form of fraudulent crime A recent report by...
Mobile Identity Authentication Many potential business-cases point to the desire to have an...
Identity fraud is rampant. Just perform a Google search on the term and the evidence to support...
Earlier this year, a car salesman in Houston was kidnapped while taking a prospective client on a...
A criminal that has your information can take over your life in a variety of different ways: he...
In our tech-based society, smartphones, tablets, and other mobile devices are central to our daily...
Accurate identification papers are essential to safeguarding financial and legal transactions as...
Recently, in Brooklyn, a man successfully made a $1,500 purchase using fake identification at a...
Deep in the underbelly of the "Dark Web's" digital black market, identity fraud and counterfeiting...
When an identity is stolen, the damage can extend far beyond the credit report of the victim. When...
Loss prevention is a many-faceted practice these days. Gone are the times when cameras on the...
At some point, every business should ask itself, “What is the easiest way to prevent fraud from...
Does your business handle in-store credit applications? Are you verifying the identifications of...
The New Year is bringing a change to the credit card industry. In the United States, credit card...
The usage of fake IDs in an in environment like a Gentlemen’s Club typically is for underage...
Warning:The following information is scary. Stop reading now unless you have a robust identity...
We have written much on the subject of the Modern Face of Identity Theft, and howtechnological...
Identity authentication is rapidly becoming an issue of great concern to the banking and other...
Sharp Spike in Fraudulent Tax Returns Reported by IRS
Our nuclear plants have become like mini-fortresses following 9/11. Concerns over attacks on land...
This article was originally published on CBinsight.com The Best Way to really "Know Your...
According to FBI statistics Identity Theft is the nation's fastest growing crime. Identity theft...
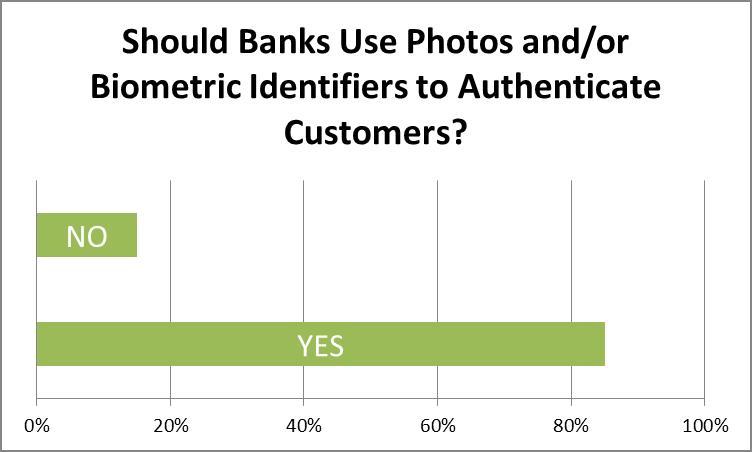
In early June this year, we conducted a survey of banking and financial professionals, asking...
In a survey of financial professionals conducted last month, FraudFighter discovered that a vast...
Faced with the extraordinary challenge of trying to bring a financial services operation into...
There are a number of ways to achieve compliance with anti money laundering regulations by...
The Bank Secrecy Act or BSA requires a written Customer Identification Program (CIP) for client...
At the heart of many acts of fraud lies the intentional misrepresentation of identity. When ORC...
Most loss prevention and asset management personnel make the mistake of thinking that shrinkage...
In a recent speech to the GOP faithful, Presidential Candidate Mitt Romney held up Arizona’s...
The world has changed much since September 11, 2001. Awareness of how fragile our way of life can...
In the past, fake ID’s have largely been associated with underage drinkers trying to get their...
I n the ongoing war against identity theft, individual battles are constantly being waged and...
“Extremely troubling,” is how one Arizona public safety officer described the small items in front...
If you have followed the news at all lately, you have likely heard that financial institutions of...
It is perhaps a sign of the times when the annual convention of anti-money laundering...
Scenario:A financial institution is opening a new branch, and is starting a major local PR blitz...
One of the biggest concerns of any financial institution – that is, any institution that routes...
The last decade brought about a tumultuous change in financial institution regulations. Many...
As if it weren’t already difficult enough to verify identity documents, now comes a new wrinkle in...
Earlier this month, FraudFighter began providing advanced sample copies of our new Driver License...
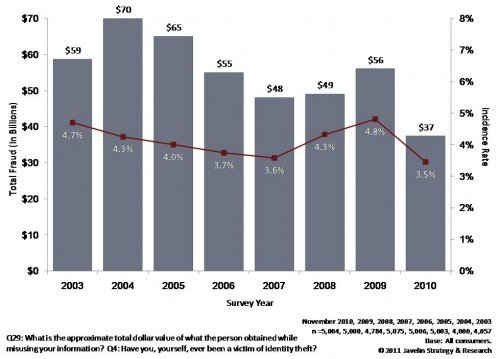
If you read Part I of our blog series on identity fraud you almost surely remember the sum totals...
Two very important studies delving into fraud reports from 2010 were issued recently. The first, a...
Rounding out our October spotlight on identity fraud and identity authentication, we have recently...
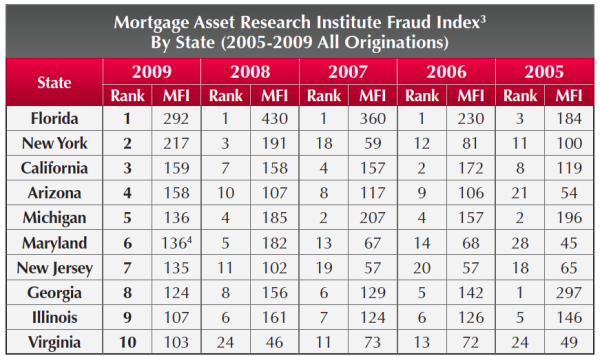
In continuing our September Mortgage Fraud spotlight, this week we are talking about the...
For anyone concerned about how mortgage fraud can affect them specifically, the LexisNexis...
Earlier this week we discussed how financial institutions place improper focus on online identity ...
International Law Enforcement Takes-Down a “Top 10” Site
As credit cards continue to supplant cash and checks as the preferred method of payment, credit...
In another great article on the National Retail Federation blogsite, Ellen Davis discusses return...
Burden, or Benefit?
Part 4 of a four-part Process for Setting-up a Red Flag Rules Compliance Policy UPDATING THE...
Casino environments are beset by opportunities to experience losses from counterfeit fraud....
Every day in the business world, organizations strive to be the best. They work to identify the...





.png)









.png)















.png)