


 Many potential business-cases point to the desire to have an identity authentication solution available as a mobile application on a smart phone or tablet. In some cases, it simply isn’t feasible to have a stationary device, tethered to a PC, available at the location where authentications must occur. In other cases, it may be desirous to have a client that is not in your physical store or branch location conduct an identity authentication wherever they are – which might be in their home, at a hotel, or even walking on the street.
Many potential business-cases point to the desire to have an identity authentication solution available as a mobile application on a smart phone or tablet. In some cases, it simply isn’t feasible to have a stationary device, tethered to a PC, available at the location where authentications must occur. In other cases, it may be desirous to have a client that is not in your physical store or branch location conduct an identity authentication wherever they are – which might be in their home, at a hotel, or even walking on the street.
Mobile IDentity Document authentication is a challenging task. In the United States, alone, there are more than 1,200 different valid types of identity document. The task of recognizing and authenticating such a large variety of documents requires significant knowledge about the documents themselves and what to look for.
Authentication with a mobile device must rely on images captured by the cameras that most iOS and Android phones now include that are of sufficient quality and clarity to allow for deep-pattern-matching. This process – deep pattern matching – compares ID images to a comprehensive identity document library with detailed information about the design of each different type of ID. FraudFighter is partnered with the leading document library companies in the world in developing its mobile authentication solution, MobilVerify.
In May 2016, an important announcement involving online identity authentication was made. The state of Alabama announced that they were implementing a system (eID) that would allow tax-filers to self-authenticate their driver license using their mobile device. The solution then allows the person to authenticate that they are the same person as pictured on the Identity Document by using the smart device to capture a selfie-image which is authenticated against their driver license photo.
The eID initiative will allow taxpayers to opt-in to a program that adds a new layer of security regarding tax return processing. eID leverages the highly trusted and secure driver’s license and ID card database managed by the Alabama Law Enforcement Agency to ensure that individuals are who they claim to be. Alabama taxpayers will be able to confidently place a “lock” on their tax ID within the Alabama Department of Revenue to be sure that tax returns are not processed in their name without their authorization. The eID is empowering participants to use their verified identities (including selfies) as a way to protect their personal transactions. The “selfie” provided by the individual filing a return can be compared to the photo on file in the DL/ID database and is used as part of the layered security process. This allows fraudulent filings to be intercepted before the individual and state are the victims of tax refund fraud.
“Tax refund fraud is a core issue for not only Alabama but all states, and we are dedicated to protecting our citizens,” said Alabama Revenue Commissioner Julie P. Magee. “This innovative initiative will allow all taxpayers to put the control in their own hands – and it specifically gives a way for those who have already had issues with identity theft to attain a level of comfort and protection that they did not have in the past.”
The two-factor process of authenticating the individual during online transactions adopted by Alabama is a ground-breaking new paradigm. A paradigm that can be implemented in online and mobile transaction environments across many industry sectors.
With mobile phone penetration nearing 70% of the U.S. adult population (a Pew Foundation poll in 2015 determined the number to be 68%) it is highly probable that an individual conducting a transaction in your online environment will have such a device available. There is a strong correlation between individuals that conduct transactions online (such as making purchases and performing banking tasks) and those that own smart phones. Of course, customers conducting mobile transactions by definition must have a mobile device.
The two-factor mobile authentication process can be used in a couple of different ways:
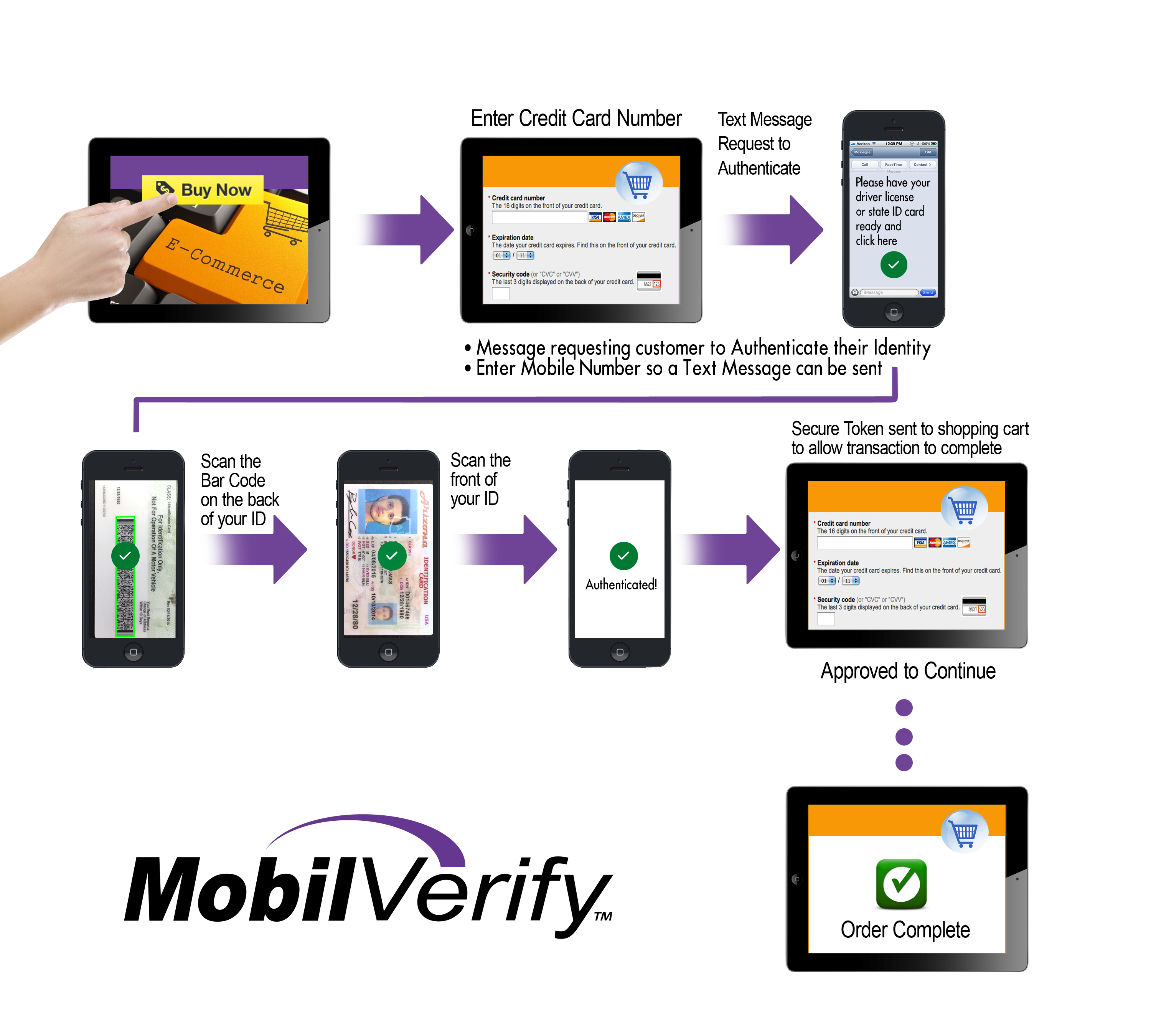
How are ID documents authenticated?
MobilVerify reads the barcode, and then compares the data to the Enhanced Security Feature (ESF) data. Note that not all ID documents have barcodes and/or an ESF. In this case, the front of the license is imaged and a deep pattern match is conducted that is similar to that conducted with the point-of-sale scanner, with the exception that only white-light (visible) images are used for authentication.
What happens to the personal data?
As a leader in fraud prevention, we take the safety and security of personal identity data very seriously. We have observed the steady increase in the instances of mass data hacking, and have researched and reported frequently about the sophistication of the criminal marketplaces that have arisen to capitalize financially on the stolen data. For this reason, we are committed to absolute security on any data that is managed by our systems.
Every process we design which in any way touches personally identifying data is built with data security in mind. Several overriding principles guide us in this approach:
What if we don’t want employees using their own smart phones?
Many organizations are quite comfortable with the “bring your own device” mentality; however, we realize that this may not be appropriate for your organization, or for the specific purpose in mind in this instance – e.g. capturing images and data from ID documents.
For this reason, FraudFighter is able to provide dedicated mobile devices to clients with Mobilverify application pre-installed at very reasonable prices.


.png)
