 There are a number of ways to achieve compliance with anti money laundering regulations by authenticating ID documents. Relying on the skill of bank managers, clerks and other front line applicant processors is not one of them.
There are a number of ways to achieve compliance with anti money laundering regulations by authenticating ID documents. Relying on the skill of bank managers, clerks and other front line applicant processors is not one of them.
There are about 600 different driver's licenses in the U.S. alone including an additional 500 specialty licenses related to off-road, motorcycles, commercial vehicles, etc. Even if one were to memorize all of the them, they change frequently enough that keeping abreast of the changes can be a full time occupation. Also, there are hundreds and hundreds of passports, government identity cards, diplomatic IDs and other official identification from countries all around the world. Knowing the difference between an authentic ID and a fraudulent one is much to involved for any one individual much less those in the financial industry whose first job is not identification authentication.
Anti money laundering laws are designed to prevent illegal cash transactions from criminal enterprises or terrorist activity. The consequences of non compliance can be severe. If your business extends, renews or continues credit you are subject to the rules regulations and penalties of the anti money laundering Red Flag Rules. Setting up a red flag program to identify transactions that require the authentication of Identification documents will keep your company in compliance and help to prevent fraudulent transactions from affecting your bottom line.
In addition to the Red Flag Rules, if your business is engaged in large cash transactions, you may be subject to the requirements and penalties associated with the Bank Secrecy Act (BSA). Verifying and authenticating identification is an essential part of BSA compliance.
Red Flag Rules
Red Flag rules were put into effect in 2003 under FACTA (Fair and Accurate Credit Transactions Act) and for the first time required financial institutions to take measures to authenticate the identification of individuals seeking to receive credit. These red flag rules set up a series of guidelines for the identification of possible transactions, so called red flags, that may be involved in identify theft and or money laundering.
There are several posts in this blog related to the Red Flag Rules, so I won't go deeply into them. For purposes of this post, the main aspect of the Red Flag Rules is the authentication of identification. Simply because someone hands you an ID does not mean it is either genuine or belonging to the person presenting it.
Bank Secrecy Act Compliance
The BSA requires any cash transaction over $10,000 to be reported. As part of the rules the identity of the person engaged in the transaction must be verified. It is no longer enough to simply copy a driver's license. The authentication of the identification must be verified. Like the Red Flag Rules having a process in place to verify the authenticity of identification is essential to compliance.
Third Party Authentication Services.
On line data authentication services are often used to verify the data associated with a given document. In other words, is the person before me the person stated in the identifying information (i.e. SS#, address, telephone etc.). There are significant short comings to using third party authenticators to verify the authenticity of a person's identity. Most of these services rely on public information databases to obtain their information. This information is readily available on the internet for a small fee and is easily accessed by someone willing to commit money laundering. Criminal records, vehicle registration, last know addresses and names and addresses of relatives are all elements of sophisticated identify theft. This data is frequently used to establish security questions for the individual. Worst of all, the data relied upon by third party authenticators can be out of date by up to as much as 6 months!
If the high failure rate attributable to many of these companies is not reason enough, the cost associated with 3rd party authenticators may exceed the cost of in house technology/ Using front line, state of the art identification authentication technology is better suited to businesses involved in large transactions or subject to the BSA and anti money laundering statutes.
Automated Document Authentication
 Here we have technological solutions for front line application processors to quickly and efficiently verify the authenticity of a particular document for anti money laundering compliance and prevention. To be clear, we are talking about determining whether a particular ID is a valid document. We are not talking here about whether the data on the document is authentic (ex. stolen identity used to obtain a valid driver's license).
Here we have technological solutions for front line application processors to quickly and efficiently verify the authenticity of a particular document for anti money laundering compliance and prevention. To be clear, we are talking about determining whether a particular ID is a valid document. We are not talking here about whether the data on the document is authentic (ex. stolen identity used to obtain a valid driver's license).
Verifying an ID document as genuine requires sophisticated optical and electronic equipment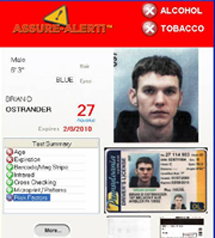 that scan for and identify document security features. Examples are; data chips embedded in the ID, digital watermarks, bar codes and magnetic and optical strip tests to see if they have been adulterated.
that scan for and identify document security features. Examples are; data chips embedded in the ID, digital watermarks, bar codes and magnetic and optical strip tests to see if they have been adulterated.
The document library associated with the device must be updated regularly and frequently to keep up with the changes in identification.
Using these devices allows the front line application processors to quickly and efficiently verify the authenticity of a particular identification document. There is no need to rely on the skill or knowledge of the employee because these devices will provide a simple pass/fail answer without the need to explain the underlying cause for the failure.
In addition the data associated with the document and the evidence that the document was scanned can be stored for later compliance in the event of fraudulent activity surfacing during the course of a federal investigation or compliance audit.
Ultimately, achieving compliance with anti money laundering statutes by authenticating ID documents is not only best business practice it is required by law. The options for authenticating ID documents are limited to on line verification services or in house automated document authentication. Using a combination of these may be the best solution for anti money laundering compliance and prevention.



