
Why AAMVA Verification is not a foolproof ID Authentication method
A criminal that has your information can take over your life in a variety of different ways: he could take out a loan in your name, he could empty your bank account, or he could even rent a car and simply not return it, leaving you with the bill. The possible uses of a stolen identity are varied and numerous to the savvy thief, but before he can truly put the stolen identity to use, he’ll need to have a physical identification card ready in order to ‘prove’ his identity whenever it is questioned. And thanks to the REAL ID Act, ‘proving’ his identity may have gotten a bit easier…
The REAL ID Act
It was 10 years ago, on May 11, 2005, that a federal standard for driver’s licenses and identification cards was mandated through the REAL ID Act. In a nutshell, the REAL ID Act mandates that state DMVs must meet new federal standards when issuing identification cards and driver’s licenses and lists the official purposes for when a federally-issued identification measure is required and when a state-issued identification measure can suffice.
A portion of the Act details the interstate requirement of data sharing through the AAMVA, which is a non-governmental nonprofit that administers and enforces laws related to motor vehicles in the United States, Canada, and, the US Virgin Islands. When issuing an identification card, each state DMV is required to give a ‘unique, identifying number’ and obtain the applicant’s:
- Full legal name
- Signature
- Date of Birth
- Gender
- Principle residence address
- Front-facing profile with a photograph
Each applicant is also required to prove his or her full legal name, birthdate, legal status, Social Security number, and principle address using a combination of the following documents:
- Birth certificates
- Passports
- Permanent resident cards
- Social Security Cards
- W-2s
- A recent utility bill (for principle addresses)
Every state DMV is required to store a digital image of each submitted document.
Although states do not have to share the digital images of submitted documents, they are, at minimum, required to share with the AAMVA all the printed data that is found on an individual’s identification card and/or driver’s license as well as any driver’s history (such as points on licenses and suspensions). Considering that the AAMVA is essentially amassing data on all persons issued a state identification card or driver’s license, steps have been taken to create a system in which identities can be ‘proven’ through AAMVA verification.
What is AAMVA verification?
AAMVA verification describes a method of verifying an individual’s identity in which a state identification card or driver’s license is run through a machine that extracts the individual’s data from the card and compares it with known data in the AAMVA database in order to ensure that the identity as depicted on the card/license is real.
The Pros of AAMVA Verification
On paper, AAMVA verification is a positive, effective step in creating a federal standard for analyzing the legitimacy of an identification card or driver’s license. It absolutely makes sense to check whether or not the identity on a presented card or license indeed exists. After all, without a database to check identities against – with unusual names such as ‘Snow’ and ‘Peregrine’ gaining popularity these days – who is to say McLovin is not a real person?
In addition, having a national database, as opposed to databases limited by state, greatly streamlines identity verification processes that take place across state lines, such as out-of-staters purchasing alcohol or renting a hotel room. Without a national database, identities would need to be verified by contacting the issuing state’s DMV.
The convenience of having a national database of identities, however, is exactly why AAMVA verification can potentially backfire and allow identity thieves easier access than ever before to individual’s identities.
The Cons
The glaring problem with AAMVA verification is that it only verifies the information found on identification cards and driver’s licenses, but does not verify whether or not the card/license itself is real. Checking the data found on an ID card or driver’s license indeed does prove whether or not such a person exists, but it does not prove whether or not said person is the one using the ID card/driver’s license. In essence, what is to stop a thief from creating a brand new card with matching data but his photo in place of the victim’s?
When it comes to identity theft, the common misconception is that hackers are only after people’s financial information, such as credit card numbers, bank account numbers, and so on, so that the hackers can go on a spending spree before the accounts are shutdown. However, hackers are often just as happy getting their hands on information that simply identifies a person, such as a full name, an address, or a Social Security number. It is because this type of information allows identity thieves to perform other types of financial actions, such as opening a bank account in the victim’s name or renting a car and not returning it (as mentioned in the first paragraph), that are as viable and demanded as the actions that can be performed using a victim’s financial information.
This type of data – the identity information individuals, not financial information of individuals – has been so sought after in the recent years that many sites on the darknet have popped up, including the infamous, but now defunct superget.info. With a few simple clicks of the mouse, anyone with the know-how could access and use your identity.
Just how easy is it for someone to assume your identity?
Currently, there are hundreds, if not thousands, of black market sites just like superget.info in which identity thieves can access in order to obtain the identity data of just about any American citizen; even Oprah Winfrey’s identity, Social Security numbers and all, can potentially be up for grabs. For a price, these black market sites will provide everything from an individual’s full name to the individual’s employer’s name.
On superget.info, for example, for just $1, thieves could target a particular individual: inputting an individual’s name and address returns that individual’s Social Security number and/or birthdate. If thieves are not that concerned about stealing particular identities, they can purchase identities in bulk; the site even provided price breaks:
- 1-499 identities = .25/identity
- 500-4999 identities = .22/identity
- 5000-9999 identities = .18/identity
- 10000-16499 identities = .16/identity
When purchased in bulk, each identity comes equipped with the individual’s:
- First, middle, and last name
- Email address
- Email password
- Physical address
- Phone number
- Date of birth
- Social Security number
- Driver’s license number
- Date of birth
- Bank name
- Bank account number
- Bank routing number
- Employer’s name
- Number of years at his/her current job
Before the site was shutdown, the owner of the site claimed “he has more than 330,000 records of this type, and is adding 300-400 new records each day”.
In short, if your identity was stolen, there was a chance that all the data mentioned above was bought for a whopping sixteen cents. After an identity thief has obtained a stolen identity, he would then need to figure out how to create a counterfeit identification card or driver’s license with the victim’s information both printed and encoded onto the card/license. Although this sounds complicated and expensive, in this day and age, it is not.
Simply Google searching “blank id cards” shows that there are a variety of affordable blank ID cards available from various merchants – there are even ID cards that already come with the magnetic stripe that is found on the backs of some identification cards and driver’s licenses. Thanks to advances in software technology, barcodes can be generated by simply “clicking a button or ticking a checkbox”. To make sure a scanned counterfeit ID returns the correct information in the correct format, all an identity thief would need to do is scan a real ID, see how the information is given, and follow the format when encoding the card.
Armed with the data from a stolen identity and a blank card, a thief can surely trick AAMVA verification by encoding the stolen data onto the card, embellishing the card to give it the look and feel of an identification card or driver’s license issued by the victim’s state, and imposing a picture of himself in place of the victim’s.
According to study published last month entitled “Victims of Identity Theft, 2014” by the Bureau of Justice Statistics:
"Among those who reported a direct financial loss, victims of personal information fraud lost an average of $7,761 or a median of $2,000 per victim, compared to victims of existing bank fraud who lost an average of $780 or a median of $200 per victim."
If a thief can put together a counterfeit identification card or driver’s license with real info for, at the most, a few dollars, but get away with, on average, $7,761 per victim, you can be sure that the stolen identity industry will show no signs of slowing down – the rate of return is just too high.
The AAMVA has more or less created a treasure trove of individuals’ data for thieves to steal by compiling everyone’s data into one database. If you feel confident that the AAMVA has the security measures in place to safeguard your information from hackers, don’t. Corporations such as Target and Home Depot have experienced massive data breaches in the past couple of years alone, and even a government agency – the Office of Personnel Management – has, last month, been the victim of a hacking scheme in which approximately 5.6 million individuals’ fingerprint images were stolen. A shrewd thief could go as far as hacking into his intended victim’s state’s DMV to access all the digital images of the most pertinent documents used to prove the victim’s identity, giving the thief even more resources to ‘prove’ his identity.
If it hasn’t been hacked already, you can be sure hackers will, at some point, target the AAMVA.
The Solution
The solution does not involve cutting out AAMVA verification – it does, consequently, have the positive effect of streamlining financial processes that involve the verification of identities across state lines. What the solution does involve is the addition of another verification measure in order to authenticate a card or license. Authentication can check whether or not the information on the card/license is real and whether or not the card itself is a real, state-issued card/license.
As mentioned above, the problem with AAMVA verification is that it does not check whether or not a card is real. Except for the most veteran of club bouncers, a well-made counterfeit ID, especially one from out-of-state, will likely bypass the scrutiny of the naked eye. Would you be able to tell which of the below IDs are fake? 
No matter how well-made a counterfeit ID is, however, it will simply be unable to bypass a verification machine. For example, five years ago, the California DMV released the new, updated design for its state identification card and driver’s license. The updates to the design included a variety of different security features that cannot be mimicked without the use of specialized, expensive machines that are typically not available for public purchase. For instance, commercial printers are simply incapable of printing the level of detail found on certain areas of the California driver’s license: 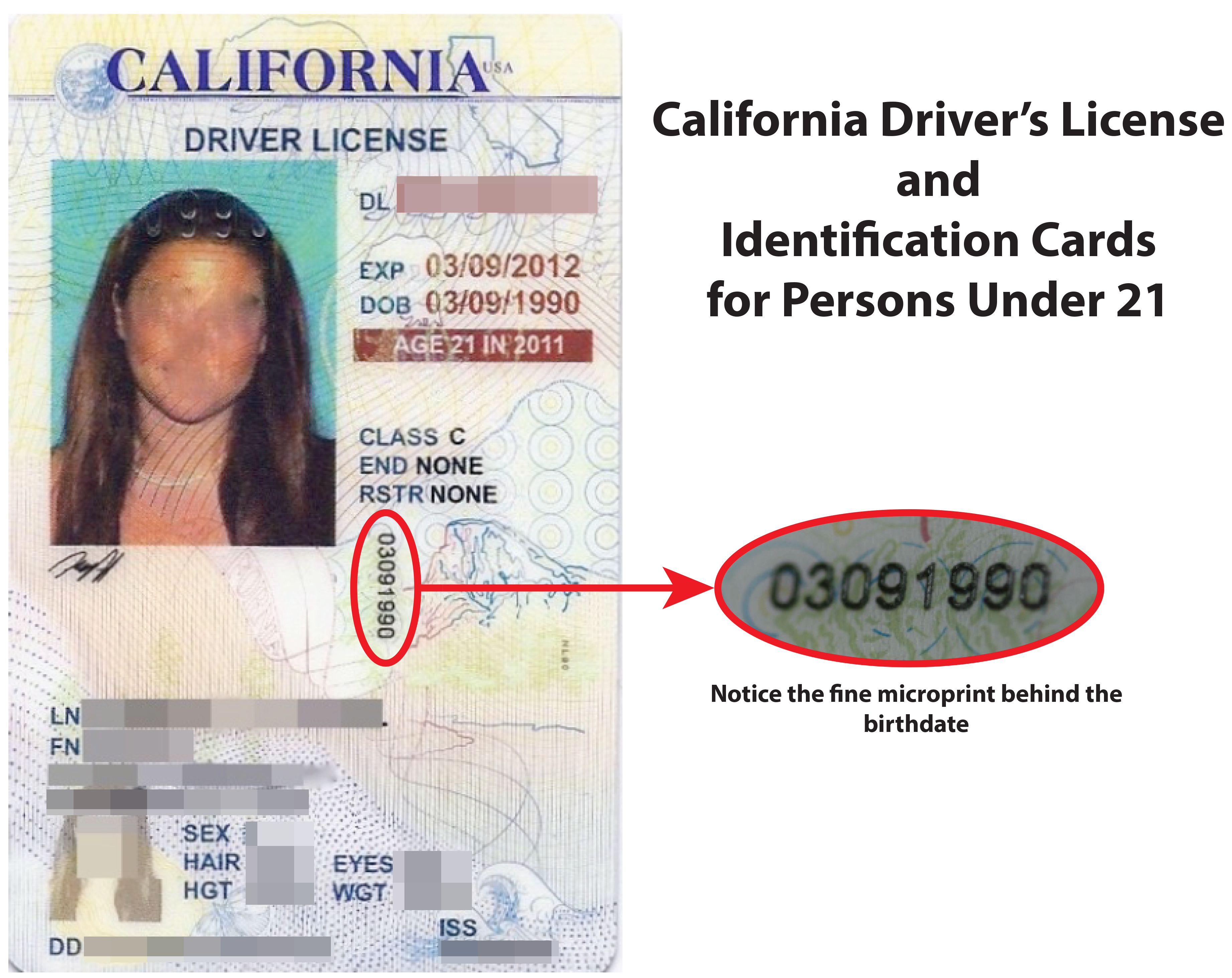
With a two-factor ID authentication method, you can be sure that the information on the ID is real and on a real, state-issued card. However, it should be noted that the downfall with only verifying that the ID is real is that an identity thief could simply use a real but stolen ID. But, by authenticating IDs using both a data-checking verification method and a card/license-checking verification method, you can be sure that not only is the ID being used is on a real, state-issued card but that the ID contains the information of a real, DMV-registered individual.
Want to learn more about ID Authentication?
Download a copy of our "Reduce Fraud with Identity Authentication" Whitepaper:
Want to protect your business with ID Authentication?
Our seasoned team of fraud prevention specialists can help evaluate the most effective ID Authentication strategy for your business:





.png)
