
The Pandemic Forced a Reckoning for Identity Authentication
Trust what we cannot see? The best security might be completely invisible and hands-off to us, with companies employing a multi-channel approach to identity authentication and account access. Experian’s recently released “2021 Identity and Fraud Report” disclosed a number of very interesting data points that revealed how consumers’ expectations of security and transactional convenience are evolving.
For the past few years, companies globally were engaged in enhanced digital “customer recognition” strategies aimed at concurrently improving the experience and security of our online shopping and banking activities. This steady burn of study and change quickly exploded into a raging fire of action as the pandemic forced companies to execute on former best-practice theories, which turned into today’s processes.
Over the past year and a half companies have had to adjust staff and schedules, re-allocate development funds to pull future projects into the current day, and scale their remote operations capacity to meet this new consumer demanded reality. To be sure, 2020 was an exercise in extreme agility, with companies scrambling to accommodate the changed “now” and prepare for the uncertain “now-what” of the next few years ahead.
That latter picture is now coming into clearer focus as Experian captured what consumers have been expressing in their actions and deeds -- that they want to do more business remotely and online, they expect it to be completely safe and secure, and also that they will not accept transactional hassles or obstacles to put in their way.
Of course, regardless of impetus or motivation, a drive toward increased remote operations could also present potent opportunities for operational efficiencies that ultimately drive profitability and growth. But concurrent with this shifted focus and direction toward remote operations capabilities, also comes the potential for increased criminal activity taking advantage of the holes in our digital security infrastructure.
Security or Convenience?
Where our digital traffic goes, criminals closely follow, knowing that there are immature systems and processes along with consumer carelessness to exploit.
As such, when it comes to ensuring the integrity and growth of our digital economy, businesses and consumers are increasingly faced with a monumentally difficult question: What do we value the most -- our Security or Convenience?
Now obviously, we cannot ever compromise or standstill on our security. The illicit techniques and technologies criminals employ continue to advance, and once they get ahold of our personal information or access to our accounts, they can cause all manner of havoc beyond a “straightforward” theft of funds.
They can exploit mere fragments of our identities to open “Synthetic” accounts in banks to fraudulently establish credit lines and “bust out”, cash in hand. They can sell our full PII (Personally Identifiable Information) stack to others of their ilk on unmonitored corners of the Dark Web. Discoveries, investigations, and repairs to this damage can take months if not years to resolve, costing consumers scads of money and causing significant mental and emotional distress.
The natural & immediate reaction to such a massive threat would be to build more walls, dig another moat around the castle, and a lay couple more drawbridges for good measure. Further, we might then require 10 sets of keys, a blood sample, and a 2-day delayed DNA test to prove who you are to let you into your account.
Of course, this is absurd. Customers would never hold 10 keys.
Bringing the security discussion closer to the realm of reality, it remains a constant, evolving conundrum for companies to balance the security they need against what their customers will accept. In their effort to build and provide uncompromising security, companies have found that there are clear limits to the hoops through which consumers will jump to accomplish their transaction goals.
In their wide-reaching research, Experian found that consumers consistently said that they would abandon a transaction if they had to wait more than 30 seconds.
What login passwords and passphrases and captchas and pet name security strategies could possibly be completed in that timeframe to ward off global gangs of organized criminals who have potentially unlimited state-sponsored resources at their disposal?
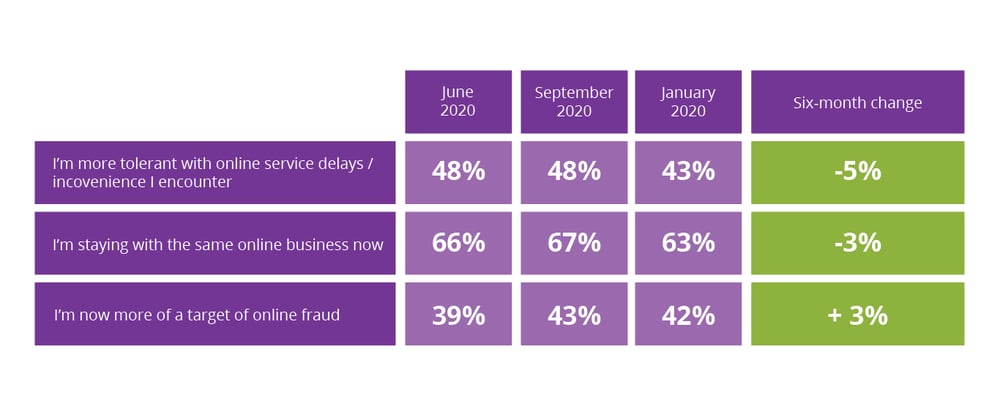
Experian also found that consumers are increasingly aware that there is more fraud out there. Consumers know that they are being targeted, but (undoubtedly maddening to businesses) are also increasingly intolerant with delays and inconvenience, and demonstrate eroding loyalty to businesses.
How Businesses can Respond
Returning to our earlier, key question – if our economy and society cannot compromise on Security, and if consumers are not willing to sacrifice Convenience (and are willing to defect from businesses), are we then at an impasse, fated to cede to the forces of crime and chaos?
Or could there be a goldilocks solution that provides enhanced security with increased consumer convenience? The answer is Yes, and consumers are ready for it.
Experian found that consumers are increasingly ready for invisible security – in fact, 60% of their consumer respondents expressed wanting businesses to implement strong, invisible security measures.
But just what is “invisible security”?
If we consider the three tenets of cybersecurity, asserting that best practice security is founded on:
1) What we know
2) Who we are
3) What we have
We are certainly familiar with the first tenet of “knowledge based” security – entering a recalled password to log into a system, or providing your last two home addresses, or the name of your mother’s maiden name. And by now we also know and understand this method’s faults, resting in the inherent hassle and insecurity with maintaining a mental (or Post-it) list of scores of passwords.
As such, the security infrastructure is turning away from measures that force us to know and recall and enter to access a secure system, and shifting towards innovative technologies that leverage covert and invisible means to verify who we are.
These are the technologies that then reference tenets #2 & #3, in inexorably linking our unique traits or ownership to our access identity.
Experian’s respondents expressed increased comfort for invisible physical and behavior-based security. Consumers ranked the following methods based on their perceived security:
1) 74% of consumers cited preference towards physical biometrics – as applicable to mobile devices (what we have) and include facial recognition and fingerprints (who we are)
2) 72% of consumers cited comfort towards usage of PIN codes sent to mobile devices (what we have)
3) 66% of consumers said behavioral analytics (who we are) should be employed, comparing historical and current unique behavior of our mouse movements, browsing location, form fill speed, etc. as captured across our PCs and mobile devices
Significantly, the use of passwords did not earn a spot in the top three most secure authentication methods, even though every digital account and device we own today requires us to enter a password or PIN. Consumers also expressed awareness that usage of our personal information and account usernames (what we know) was the least secure method to ensure account security.
All this data is a positive indication that our society may soon be ready to shift away from the realm of (insecure) passwords. However, a key caveat in the form of Privacy will inevitably (and legitimately) rear its head.
Our society is already struggling to understand and contend with what the likes of Facebook or Google do with all of the data that they have on us, as a result of mass social media over-sharing and default opt-ins.
It is one thing to know where I have hiked on a given day or what my Etsy purchases might reveal about my living room decor. It is entirely another to have my fingerprint, voiceprint, eye scan, or behavioral patterns now stored and accessed in possibly many different business databases.
Identity Authentication and Privacy
Returning to the core conundrum – if we cannot compromise on Security, and if consumers reject Inconvenience, then will personal Privacy have to be sacrificed or compromised to accommodate the former two?
Indeed, the ideals and principles of privacy might soon stand at an existential crossroad, if only because there exist far greater threats to our progress as a society and economy. Our current-day grousing of privacy erosion as manifest in focused marketing may seem quaint to the next generation of consumers.
Today's “marketed-to-natives” give no thought to cultivated ads that pop up on screen/s, proactive reminders of our next doctor appointment, or a location ping indicating we are just around the corner from a new fusion sandwich shop.
In every successive generation, it is not surprising that younger consumers embrace new technologies in greater numbers and speed than their forebearers. Experian’s research found that younger consumers are in fact more aware and concerned of the fraud risks they are exposed to and that they understand and expect technology to step in and present solutions.
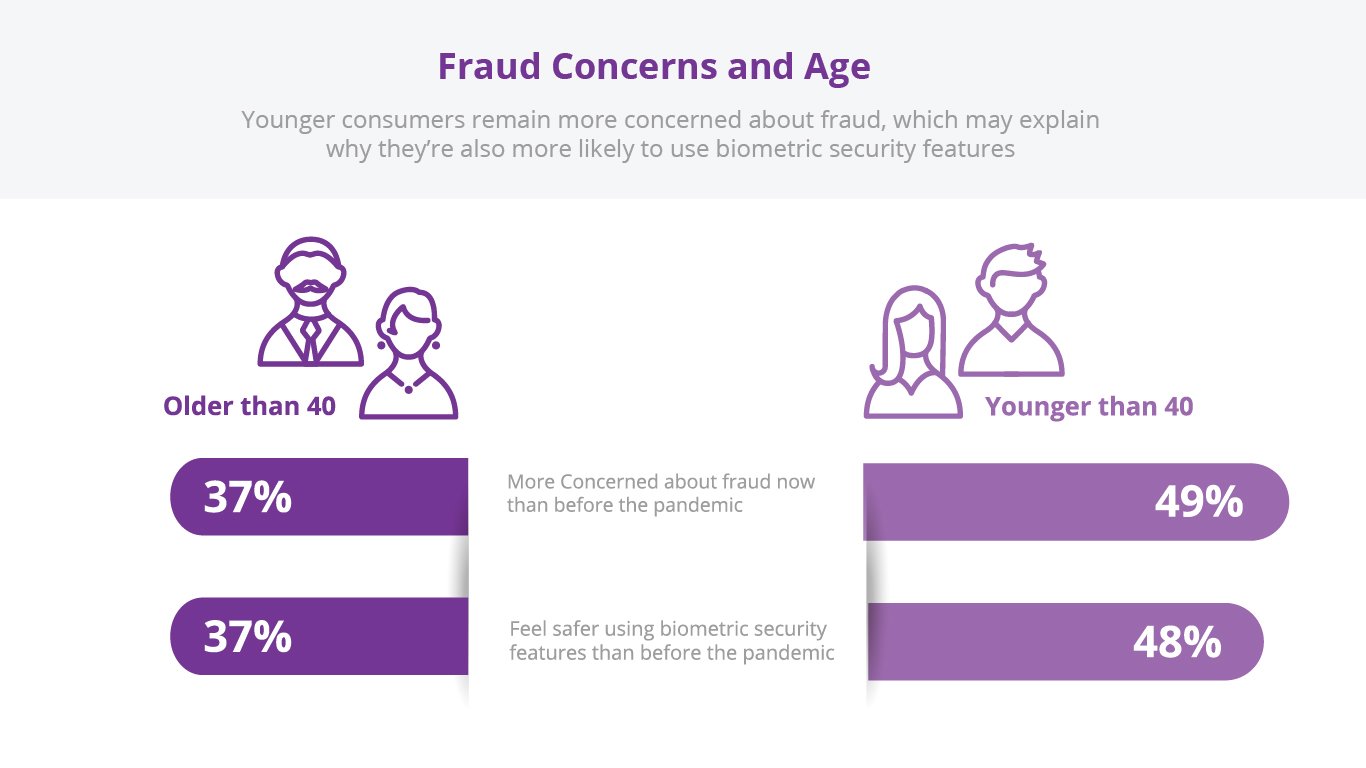
What is perhaps less clear is whether we are still truly having the “Security & Convenience vs. Privacy” debate in June 2021, or have conditions already tipped us over the precipice, snowballing our way down an unfamiliar mountain laden with policy bumps that we will just have to navigate and manage along the way?





.png)
