Recent Posts
I n the ongoing war against identity theft, individual battles are constantly being waged and...
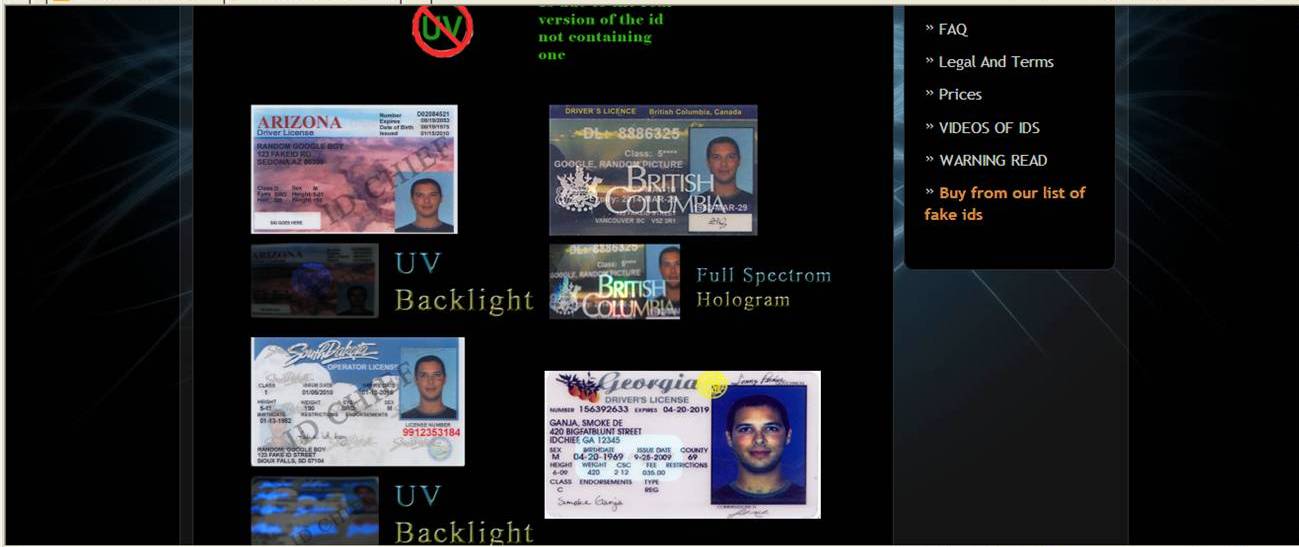
“Extremely troubling,” is how one Arizona public safety officer described the small items in front...
If you have followed the news at all lately, you have likely heard that financial institutions of...
It is perhaps a sign of the times when the annual convention of anti-money laundering...
One of the biggest concerns of any financial institution – that is, any institution that routes...
The last several weeks have seen a number of noteworthy arrests for money laundering. A fugitive...
The last decade brought about a tumultuous change in financial institution regulations. Many...
Every so often an identity fraud story comes along in the news that is not only impressive in its...
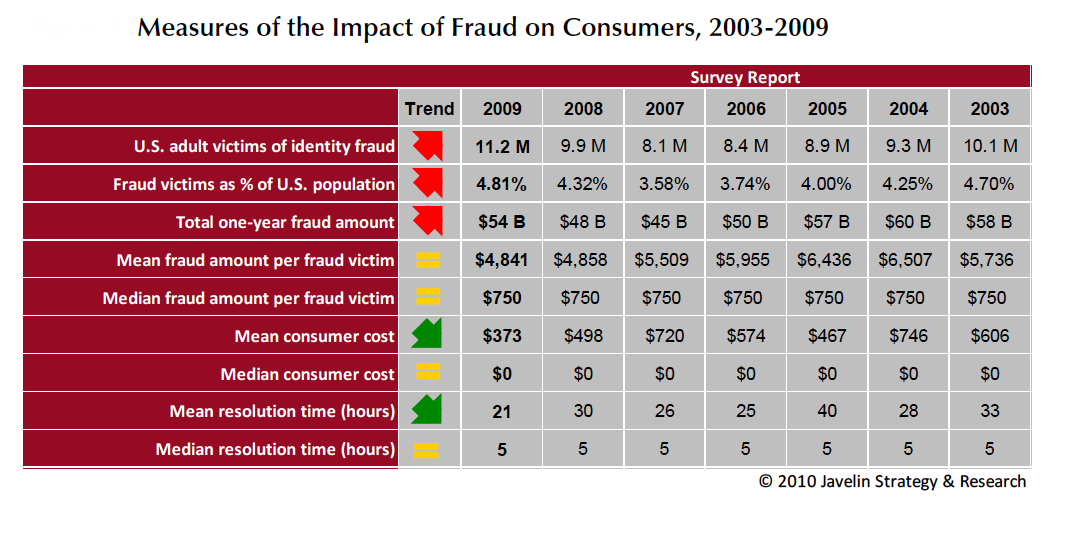
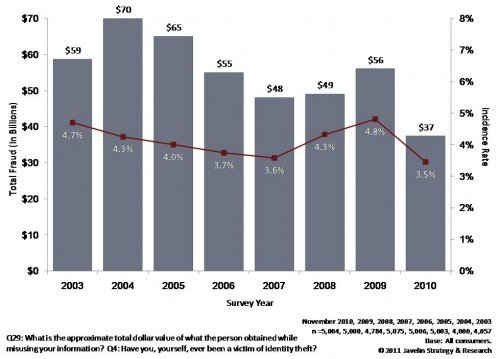
If you read Part I of our blog series on identity fraud you almost surely remember the sum totals...
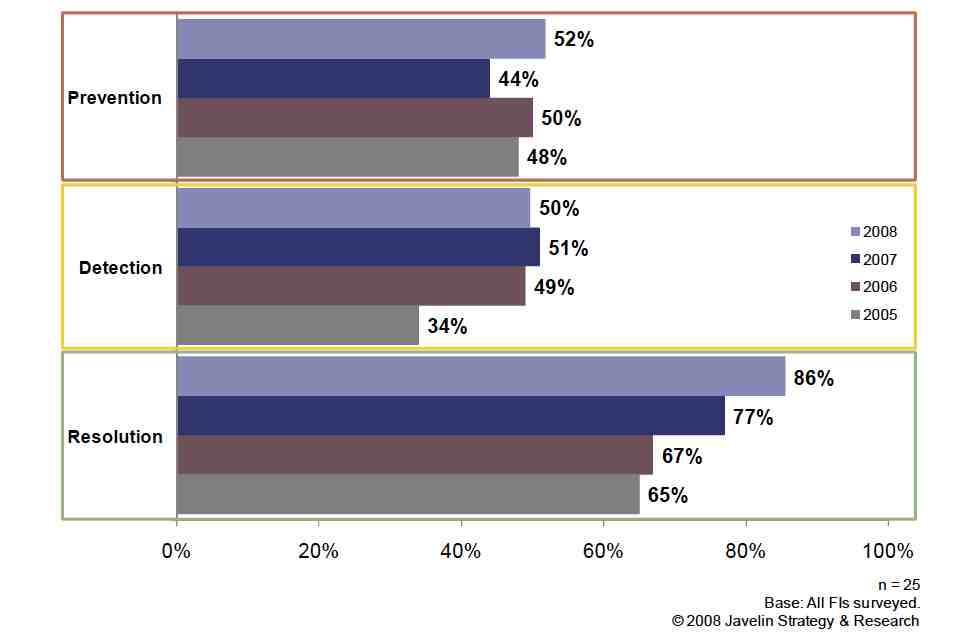
Two very important studies delving into fraud reports from 2010 were issued recently. The first, a...
Credit card processing servers. Poorly secured corporate networks. Point-of-sale terminals in gas...
Imagine you were offered this amazing business opportunity: you would join an effort by a local...
We have mentioned in a number of previous posts the international nature of many counterfeit money...
How easy is it to create counterfeit money? Up until a few months ago, the Reid brothers would...
(Note: This is the second article in our series Best Practices for Counterfeit Detection. For the...
Want an entertaining dinner party activity? Ask people around the table if they know how to tell...
Good news from the front in the battle against identity theft! Well, somewhat good news. With an...
It is always a treat to hear from actual identity thieves: understandably they are not often...
Go into any of tens of thousands of restaurants, bars or retail stores these days, and chances are...
On the heels of last week's story about Australian airline tickets bought with counterfeit credit...
Out of the three groups affected by retail fraud – consumers, financial institutions and merchants...
We have mentioned in our previous posts that fraud committed on a stolen credit card affects three...
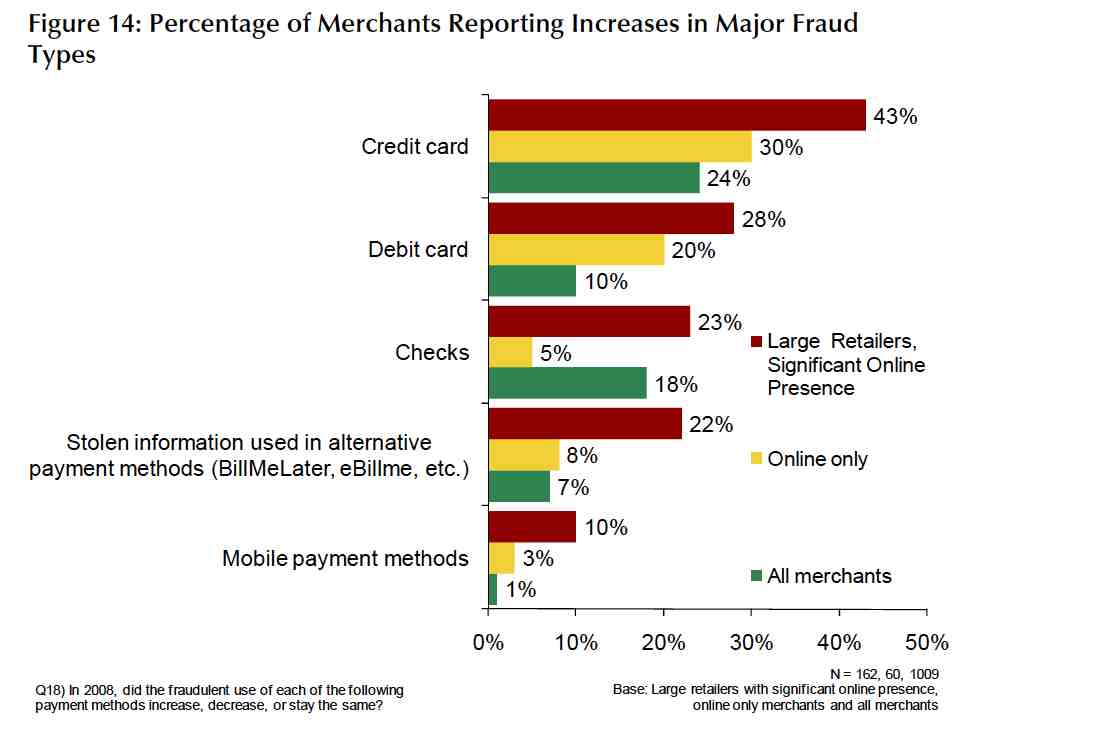
As we mentioned in our previous post, the impact of retail fraud on businesses and financial...
Rounding out our October spotlight on identity fraud and identity authentication, we have recently...
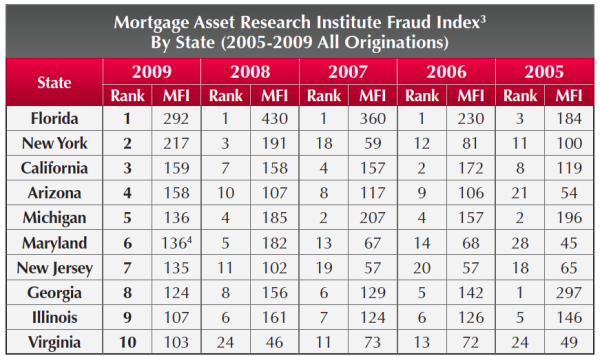
In continuing our September Mortgage Fraud spotlight, this week we are talking about the...
For anyone concerned about how mortgage fraud can affect them specifically, the LexisNexis...
It has been somewhat of an open secret that North Korea is the single biggest manufacturer of...
Hardly a day goes by without a news report mentioning identity theft or giving a heart-rending...
We have talked in previous posts about international financial fraud as it relates to employment...
Money counterfeiting, as any other crime, doesn't stand still. Fraudsters continually evolve...
So far, we have been discussing the problem of counterfeiting only within the U.S., although it...
This past Sunday's Los Angeles Times featured an article quoting Fraud Fighter's own VP of Sales...
We mentioned previously the intaglio printing process that creates fine lines around the portraits...
As credit cards continue to supplant cash and checks as the preferred method of payment, credit...
We have mentioned here previously the new high-tech anti-counterfeitting features of the new $100,...
Big-box stores are a favorite target of fraudsters, because of the value of their products. So...
Imagine for a moment you are a modern-day Al Capone. Through a combination of robbery, embezzlement...


























.jpg)