webinar
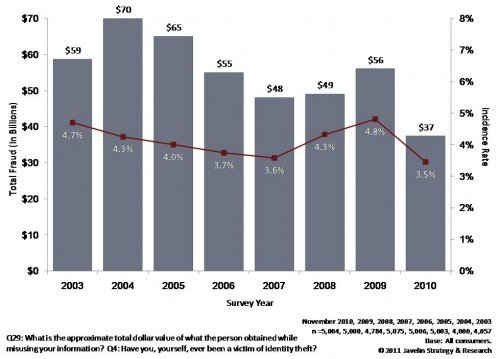
If you read Part I of our blog series on identity fraud you almost surely remember the sum totals...
Two very important studies delving into fraud reports from 2010 were issued recently. The first, a...
Rounding out our October spotlight on identity fraud and identity authentication, we have recently...